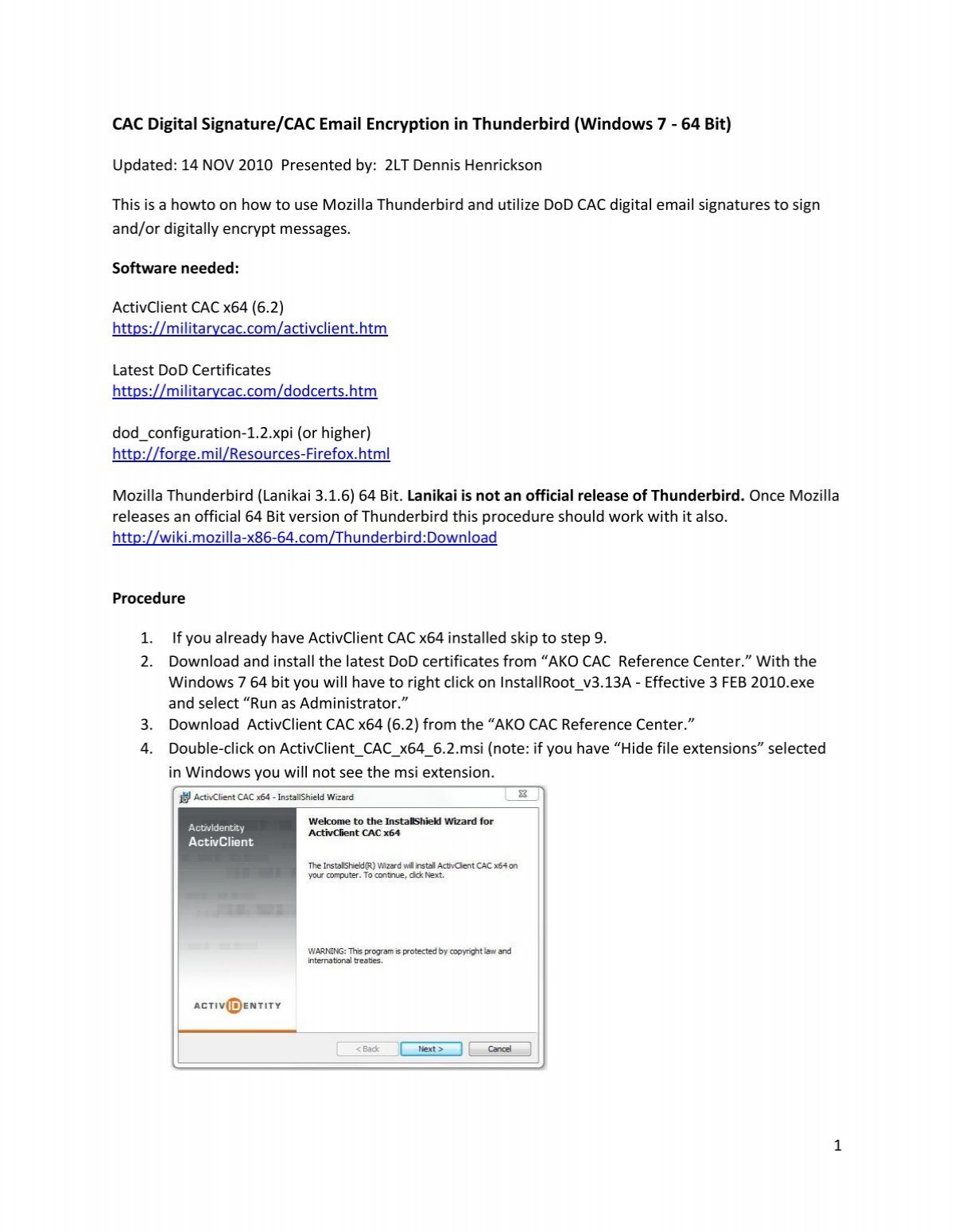
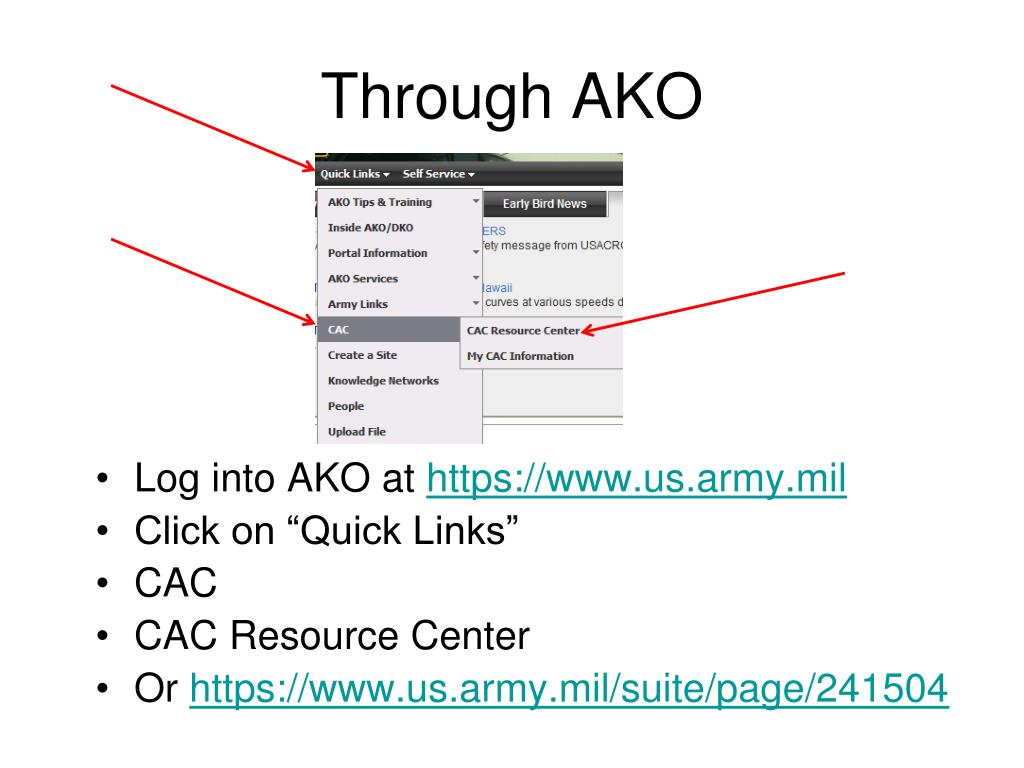
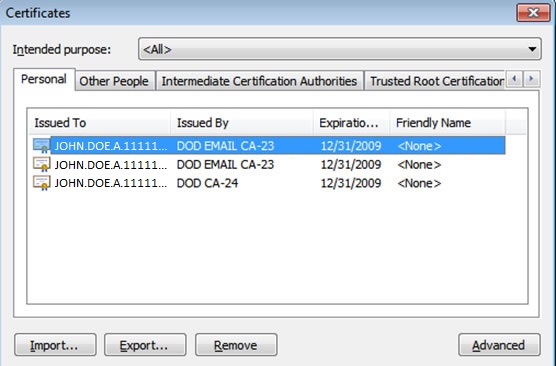
Remote Setup of PC/Laptop with CAC Reader: Step 1: Obtain a CAC Reader from ITD and Install CAC Reader Driver. Step 2: Install DoD Certificates. Step 3: Install ActivClient. Step 4: How to use your CAC. Step 1: Obtain a CAC Reader and Install Driver. CAC Reader Options: SCR-3310v2 SCR-331. Plug in your CAC Reader. An X.509 smart card (CAC, PIV or PIV-I), step up your efforts to enable its use for accessing facilities and IT resources or risk losing funding. For government IT and security professionals, the. Setting up your Account to Digitally Sign E-mails. Insert your CAC card to verify that your CAC card contains your USNA email address. Select the Active client icon on the control panel and open your card. DO NOT REMOVE YOUR CAC! It needs to be inserted at all times during this process. Open the folder ‘My Certificates.’ 3. SOLUTION FOUND!!! There is an opensource software called 'Smart Card Manager' which is referenced on militarycac.com as an alternative to using ActivClient 6.2 (AKA for those of us that can't access a CAC secured site to download a program designed to enable the use of a CAC card needed for said site). May 23, 2009 Hello sherretz, I believe your problem is with the antiquated version of Active Card Gold. If you are running Windows 7, you will more than likely need the ActiveClient 6.1. Is the Windows 7 considered 64 bit? If so, you would need the ActtivClient 6.1 for Vista 64 bit.
-->APPLIES TO: SQL API
Certificate-based authentication enables your client application to be authenticated by using Azure Active Directory (Azure AD) with a client certificate. You can perform certificate-based authentication on a machine where you need an identity, such as an on-premises machine or virtual machine in Azure. Your application can then read Azure Cosmos DB keys without having the keys directly in the application. This article describes how to create a sample Azure AD application, configure it for certificate-based authentication, sign into Azure using the new application identity, and then it retrieves the keys from your Azure Cosmos account. This article uses Azure PowerShell to set up the identities and provides a C# sample app that authenticates and accesses keys from your Azure Cosmos account.
Prerequisites

Install the latest version of Azure PowerShell.
If you don't have an Azure subscription, create a free account before you begin.
Register an app in Azure AD
In this step, you will register a sample web application in your Azure AD account. This application is later used to read the keys from your Azure Cosmos DB account. Use the following steps to register an application:
Sign into the Azure portal.
Open the Azure Active Directory pane, go to App registrations pane, and select New registration.
Fill the Register an application form with the following details:
- Name – Provide a name for your application, it can be any name such as 'sampleApp'.
- Supported account types – Choose Accounts in this organizational directory only (Default Directory) to allow resources in your current directory to access this application.
- Redirect URL – Choose application of type Web and provide a URL where your application is hosted, it can be any URL. For this example, you can provide a test URL such as
https://sampleApp.comit's okay even if the app doesn't exist.
Select Register after you fill the form.
After the app is registered, make a note of the Application(client) ID and Object ID, you will use these details in the next steps.
Install the AzureAD module
In this step, you will install the Azure AD PowerShell module. This module is required to get the ID of the application you registered in the previous step and associate a self-signed certificate to that application.
Open Windows PowerShell ISE with administrator rights. If you haven't already done, install the AZ PowerShell module and connect to your subscription. If you have multiple subscriptions, you can set the context of current subscription as shown in the following commands:
Install and import the AzureAD module
Sign into your Azure AD
Sign into your Azure AD where you have registered the application. Use the Connect-AzureAD command to sign into your account, enter your Azure account credentials in the pop-up window.
Create a self-signed certificate
Open another instance of Windows PowerShell ISE, and run the following commands to create a self-signed certificate and read the key associated with the certificate:
Create the certificate-based credential
Next run the following commands to get the object ID of your application and create the certificate-based credential. In this example, we set the certificate to expire after a year, you can set it to any required end date.
The above command results in the output similar to the screenshot below:
Configure your Azure Cosmos account to use the new identity
Sign into the Azure portal.
Navigate to your Azure Cosmos account, open the Access control (IAM) blade.
Select Add and Add role assignment. Add the sampleApp you created in the previous step with Contributor role as shown in the following screenshot:
Select Save after you fill out the form
Register your certificate with Azure AD
You can associate the certificate-based credential with the client application in Azure AD from the Azure portal. To associate the credential, you must upload the certificate file with the following steps:
In the Azure app registration for the client application:
Sign into the Azure portal.
Open the Azure Active Directory pane, go to the App registrations pane, and open the sample app you created in the previous step.
Select Certificates & secrets and then Upload certificate. Browse the certificate file you created in the previous step to upload.
Select Add. After the certificate is uploaded, the thumbprint, start date, and expiration values are displayed.
Access the keys from PowerShell
In this step, you will sign into Azure by using the application and the certificate you created and access your Azure Cosmos account's keys.
Initially clear the Azure account's credentials you have used to sign into your account. You can clear credentials by using the following command:
Next validate that you can sign into Azure portal by using the application's credentials and access the Azure Cosmos DB keys:
The previous command will display the primary and secondary primary keys of your Azure Cosmos account. You can view the Activity log of your Azure Cosmos account to validate that the get keys request succeeded and the event is initiated by the 'sampleApp' application.

Access the keys from a C# application
You can also validate this scenario by accessing keys from a C# application. The following C# console application, that can access Azure Cosmos DB keys by using the app registered in Active Directory. Make sure to update the tenantId, clientID, certName, resource group name, subscription ID, Azure Cosmos account name details before you run the code.
This script outputs the primary and secondary primary keys as shown in the following screenshot:
Similar to the previous section, you can view the Activity log of your Azure Cosmos account to validate that the get keys request event is initiated by the 'sampleApp' application.